Current solutions are a trade-off of between Security and Usability
Security-Centric design is full of friction and a waste of time.
UsabilityCentric design is vulnerable and has blind spots.
Security

Usability
CURRENT SECURITY-CENTRIC SOLUTIONS
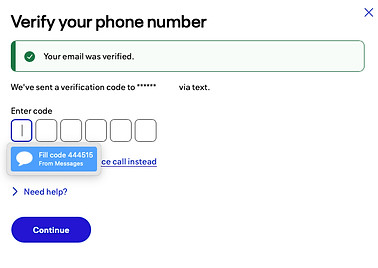
Multi-Factor Authentication
Automatic Timeout
Poorly Designed Security-Centric Security solutions are Broken
-
Annoyance to the user.
-
Wasted time, especially when a code is not received or the second device is not with the authorized user.
-
Unnecessary cumbersome process
-
If the other device is not near or an alternative method needs to be chosen, this leads to FRUSTRATION.
Current Solutions Lead to Circumvention of Security
It’s time to stop the endless seesaw between Security and Usability in authentication.

Usability
Security

A new paradigm has arrived.
For Your Eyes Only™
Authorization
Authentication today leaves more to be desired.
It's an Annoyance, a Waste of Time and often Just Security Theater. Let's stop putting up with outdated static solutions. It's time for FYEO™.

Full of Friction
Waste of Time
Vulnerable
Usability-centric
Security-centric
Blind Spots
"Just Security Theater"
"Circumvention of Security"
Security-Centric Design
HIGHER SECURITY AT THE EXPENSE OF USABILITY.

User Friction
Waste of Time
Security
Usability
SECURITY-CENTRIC DESIGN
Security-Centric = Friction & Wasted Time

CURRENT SECURITY-CENTRIC SOLUTIONS
Poorly Designed Security-Centric Security
-
Annoyance to the user.
-
Wasted time, especially when a code is not received or the second device is not with the authorized user.
-
Unnecessary cumbersome process
-
If the other device is not near or an alternative method needs to be chosen, this leads to FRUSTRATION.

SECURITY-CENTRIC REALITY
The Downstream Consequences
"CIRCUMVENTION OF SECURITY"
Users will find ways to circumvent security. Security posture can be compromised by user if the user has the ability or finds a way to circumvent the friction of authentication.
WHY FRICTION YIELDS CIRCUMVENTION
Drawing a Succinct Causal Chain




Choosing usability creates a direct security weaknesses (exposed credentials, shared access audit gaps)
Attackers exploit technical and human weaknesses (social engineering, weak recovery), making MFA ineffective when implemented or used poorly.
Users is led to favor usability-centered workarounds (sticky notes, password sharing, “leave it logged in”)
High friction (time cost, cognitive cost, repeated auth during shift work) + high perceived risk of delay
High Friction
Seek Usability
Weak Choice
Circumvention




These are rational adaptations by users who prioritize core job tasks over the secondary task of securing systems.
Usability-Centric Design
HIGHER USABILITY AT THE EXPENSE OF SECURITY.

Vulnerable
Usability
Blind Spots
Security
USABILITY-CENTRIC DESIGN
Usability-Centric = Vulnerable & Blind Spots
CURRENT USABILITY-CENTRIC SOLUTIONS
Poorly Designed Usability-Centric Security
-
Gives anyone who has access to endpoint the keys to the data kingdom.
-
Creates an unsafe security standard for access and allows the user to skip "security hurdles" friction.
-
Users option is to lower security in the name of usability. Bringing down security defenses.
-
Poor design, granting enhanced usability, but at the cost of erasing the first line of security defense.

USABILITY-CENTRIC REALITY
Downstream Consequences
"Just Security Theater"
Users often choose convenience over security—lowering their own protection just to avoid friction. This flawed design leaves endpoints, users, and entire businesses exposed, risking both data and reputation in the name of “ease of use.”

It’s time to end Security Theater—the illusion of safety that only makes users feel secure. True security can’t depend on users turning down their own defenses.
OTHER SECURITY BLIND SPOTS
We are currently not protecting unattended devices as well as we should. There are vulnerabilities and weaknesses currently present that are not being addressed. It is a growing problem as more people are working remote and accessing sensitive, personal and proprietary information from locations that are not secure and full of random people that could easily gain access to to a device or a logged in session.

Not Human-Centric
-
Doesn't Proactively Protect "Field of View"
-
Doesn't look for Shoulder Surfers and protect sensitive information from visual hacking.
-
3M Study concluded that 88% of the time a visual eavesdropper successfully acquired sensitive data.
Administrators are stuck between a rock and a hard place, they don't want to take their standard security to the highest security because the tradeoff on user experience.
What if there wasn't a tradeoff or balancing act
What if you could have the best of both worlds

No More Balancing Act


It's time for a new paradigm.
Let's bolster security AND not sacrifice usability.
And let's cover those "blind spots"

PATENTED


Enhance Usability, Security and Efficiency
For Your Eyes Only™
Authorization SDK

CONTINUOUS BIOMETRIC AUTHENTICATION
FOR YOUR EYES ONLY AUTH.
Minimize Risk
Reduce your attack surface area for remote workers.
Strengthen Defenses
Security Posture now protects from shoulder-surfing.
Improve Usability
Improve usability while bolstering security all at once.
Fewer Errors
Security that reduces the risk of Human-error.
Increase Efficiency
Users seamlessly are authorized in a blink of an eye.
With Whisper & FYEO
You can Power a New Level of Authorization
FYEO Auth enforces the core principles of Zero Trust security assurance. It's time for authentication to move beyond one-time. It's time for continuous Zero Trust authorization.

For Your Eyes Only
F.Y.E.O.
Enhanced User Experience
No Blind Spots
Zero-Trust Assurance
Shoulder Surfing Protection
Frictionless Access
Workflow Efficiency
Unattended Device Protection

FYEO Auth bridges the gap between usability-first and security-first design—delivering both, without compromise.
Its real-time authorization engine continuously verifies trust in the background, enhancing security without slowing users down.
No added steps, no extra friction—just seamless, always-on protection that makes security effortless.

FYEO is Stronger (Zero Trust) Assurance
Create a For Your Eyes Only (FYEO) environment in which no improper sharing or prying eyes can access endpoints & information therein. Ensure authenticity of users with unparalleled confidence.
FYEO is Enhanced Experience
Don't give users the friction of MFA or other current standards. Give them frictionless and effortless FYEO privacy and security. Increased level of user trust leads to a higher retention and LTV.

HOW FYEO PROTECTS YOU
For Your Eyes Only Auth.

YOUR EYES ARE THE KEY
ELIMINATE SHOULDER SURFING

NOT VIEWING YOUR DATA, YOU ARE SAFE


INSTANT ACCESS, INSTANT SECURITY

Your Eyes Are The Key


Seamless access to information. All the user has to do is view their screen and they are in, instantly. Ensuring that only an authenticated eyes are viewing their respective data. It is an experience that is frictionless for any stakeholder accessing data, in office or remotely.
Eliminate Shoulder Surfing
Protect information from knowingly or unknowingly improper sharing and potential fraud is an essential cybersecurity concern for all businesses.
Shoulder Surfing is a problem for remote work and remote access to data. Protecting information from improper sharing and potential fraud is an essential cybersecurity concern for all businesses.


Not Viewing Your Content, Don't Worry, You're Safe

With FYEO, the instant you are not looking at your device, the information is secure. Since your eyes are the key to view the content, you can customize and choose to lock it as soon as you like. FYEO gives you the ability to adjust how quickly eye tracking is off screen before securing and obfuscating the data.
Instant Access, Instant Security


With FYEO, the instant the user is not in the field-of-view of their device, the information is secure. No need to turn off a device, log-out or put the device in sleep mode. True peace-of-mind that you are instantly secure when you leave AND when you come back in the field-of-view you'll instantly continue where you left off. No wasted time, No unnecessary security hurdles. Just secure, efficient, Human Centric Authorization.


Protect Your Organization and Users with
FYEO Authorization
FYEO OFFERINGS
White-Label FYEO
FYEO for Mobile is a lightweight SDK that brings continuous, biometric-based authorization to any mobile app. Licensed and fully white-labeled, it gives businesses the ability to protect users and data without adding friction. With FYEO, only the authorized, live human behind the device maintains access—continuously.
Resell/Upsell FYEO
FYEO SDK unlocks a new category of intelligent authorization that blends continuous biometric protection with seamless usability. For partners, it represents a powerful opportunity to upsell, resell, and differentiate through patented security technology that clients increasingly demand in a zero-trust world.
Try our FYEO App
FYEO Messaging is the first communication app that ties message decryption to verified human presence. Each message, file, or video is viewable only while the authorized recipient is physically present. If another face or camera appears, the screen blurs instantly—ensuring “For Your Eyes Only” truly means it.
Prevent Fraud
Protect your users, assets and data by preventing fraud before it occurs. Losing money or trust from fraud can be devastating. Block unauthorized access. Step up your anti-fraud security tools and best practices.
Reduce Friction
Give your users the privacy & security experience they desire. Passwordless Biometrics have laid the groundwork for our always verify privacy & security. Users have more privacy and security with less friction than current standards.
Combat Attacks
Protect your assets from both digital and physical unauthorized access with zero-trust technologies ready for not only today, but tomorrow's attacks as well. Give your users the 360 degree protection they deserve.

Why Human-Centric FYEO Matters Now
Security is no longer a backend concern—it must be integrated into the user experience from the start. Yet many organizations still wrestle with the false dichotomy between security and usability.
Security and usability are not on opposite ends of a spectrum—they are interdependent. The future demands Human-Centric adaptive, intuitive systems that protect without obstructing.
Don’t wait to be overtaken. The Whisper Company offers a way to lead: with best-of-breed security solutions that require no trade-offs.
Our QRE Solution