Encryption meet Quantum

Encryption is the foundation of modern-day communication, and it is the process of encoding information so that only authorized individuals can access it. The importance of encryption cannot be overstated, as it helps protect sensitive information from cybercriminals, hackers, and other unauthorized individuals.
However, as technology continues to evolve, so do the threats posed by malicious actors seeking to breach encryption. The rise of quantum computing is one such threat that has the potential to break current standards of military-grade encryption.

Quantum: Qubits, Shor, Grover and Entanglement
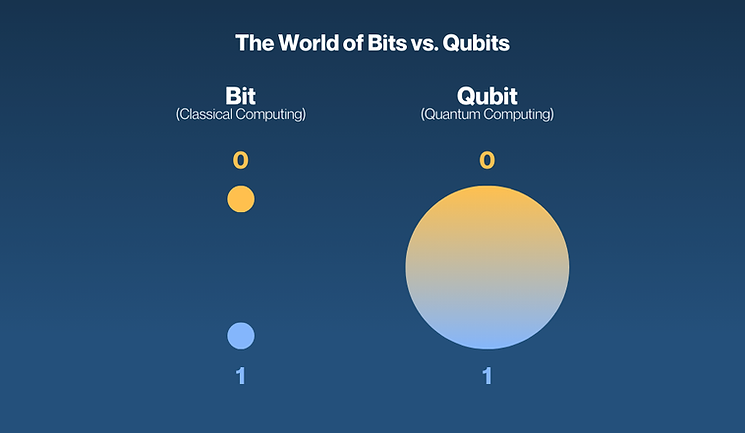
Classical computers think in bits — 0s or 1s.
Quantum computers think in qubits — which can be 0 and 1 at once, enabling exponential parallel processing.
-
Shor’s Algorithm: breaks RSA and ECC by factoring numbers exponentially faster.
-
Grover’s Algorithm: halves the strength of symmetric encryption like AES-256.
-
Entanglement: links qubits so they act as one, multiplying power.
Quantum & QUBITS
-
Quantum computing is a new form of computing that relies on quantum bits, or qubits, which can exist in multiple states simultaneously.
-
Unlike traditional computing, which uses binary digits (bits) that can only exist in two states (0 or 1), qubits can exist in multiple states simultaneously, making quantum computing much faster and more powerful than traditional computing.

Today’s most advanced quantum processors have over 1,000 qubits. It won’t take long before they reach the millions needed to make traditional encryption obsolete.
1,000 Qubits
Quantum & Shor's Algorithm
Quantum computers use qubits that can be in superpositions and become entangled. Those properties let quantum algorithms solve some problems exponentially faster than classical algorithms. Most relevant for everyday security: Shor’s algorithm would let a sufficiently large quantum computer factor large integers and compute discrete logarithms efficiently — which means it could break RSA and elliptic-curve cryptography.










