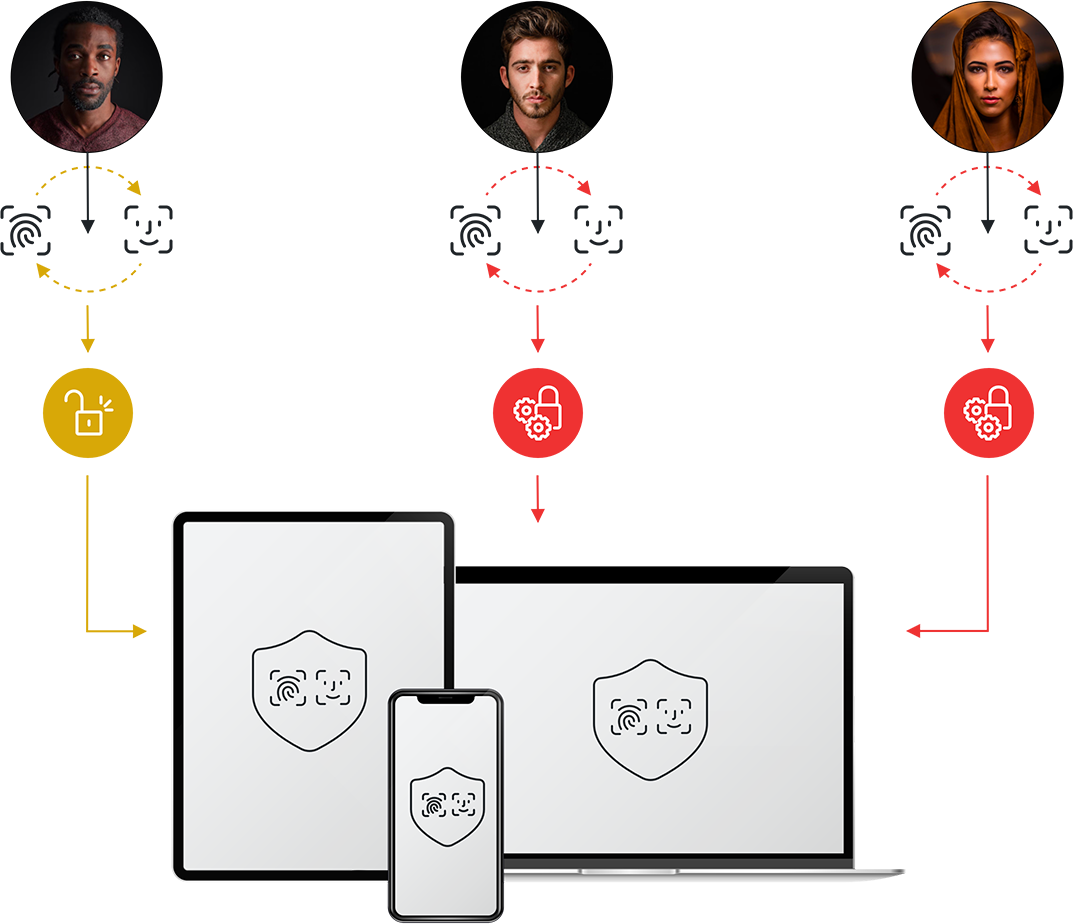
SEE HOW CONTINUOUS AUTHENTICATION PROTECTS FROM THE “HUMAN”
SHOULDER SURFING
Aka Visual Hacking or Visual Eavesdropping
It is the act of obtaining sensitive information by looking over someone’s shoulder. It is now more of an issue than ever. We can’t control the work environment and who is behind the endpoint and that window to proprietary information when so much of the workforce is remote and not in the office.
CONFISCATED DEVICE
Aka Visual Hacking or Visual Eavesdropping
It is the act of obtaining sensitive information by looking over someone’s shoulder. It is now more of an issue than ever. We can’t control the work environment and who is behind the endpoint and that window to proprietary information when so much of the workforce is remote and not in the office.
FORGETTING TO LOGOUT
Aka Visual Hacking or Visual Eavesdropping
It is the act of obtaining sensitive information by looking over someone’s shoulder. It is now more of an issue than ever. We can’t control the work environment and who is behind the endpoint and that window to proprietary information when so much of the workforce is remote and not in the office.
IMPROPER DEVICE SHARING
Aka Visual Hacking or Visual Eavesdropping
It is the act of obtaining sensitive information by looking over someone’s shoulder. It is now more of an issue than ever. We can’t control the work environment and who is behind the endpoint and that window to proprietary information when so much of the workforce is remote and not in the office.
-

LOGIN
-
ACCESS GRANTED
 STEP-UP AUTH
STEP-UP AUTH BLOCK
BLOCK
ACTION
-

RISK ASSESMENT
SEE HOW CONTINUOUS AUTHENTICATION PROTECTS FROM THE “HUMAN”
Continuous authentication is a security shift from the old model of “Periodic Authentication” where users were only authenticated once to access the network, to a “Zero Trust” model where users are continuously authenticated during their entire session.
With the increase in remote work, and company devices exposed, Continuous Authentication of endpoint devices is more important than ever.
PRODUCTIVITY AND SECURITY THROUGH ZERO TRUST

THE RIGHT PEOPLE

HAVE THE RIGHT LEVEL OF ACCESS

TO THE RIGHT RESOURCES

IN THE RIGHT CONTEXT

THAT IS ASSESSED CONTINUOUSLY

THERE IS A BLIND SPOT
The current standard is not enough
Once the session is started, a regular two-factor authentication solution won’t reverify a user’s identity. Continuous Biometric Authentication fills this security gap.
ONLY AUTHENTICATED USER GETS ACCESS TO INFORMATION BY CHECKING BIOMETRICS CONTINUOUSLY
LEARN HOW TO IMPROVE YOUR SECURITY POSTURE WITH PUA
DEVELOPER FRIENDLY EASY INTEGRATION
In a few lines of code, you can add Whisper’s PUA to your Application.
REDUCE RELIANCE ON OTPS AND REMOVE FRICTION
MFA NEEDS TO EVOLVE
- Passwords and OTPS are vulnerable to social engineering and other fraud vectors
- Friction negatively impacts consumer experience and revenue
- Password resets 7 OPTs cost firms millions annually

ENTER PUA CONTINUOUS AUTH
- Reduce reliance on OTPs and passwords by enabling 1-tap passwordless login or step-up auth
- Authenticate any device anywhere via app push notifications or biometrics
- Reduce authentication costs by cutting out OTP and Password Reset charges
AUTHENTICATION STANDARDS ARE LACKING. NOT PROTECTING THE HUMAN.

ONLY UPON ACCESS
Standard authentication only ensures that the authenticated user was there upon entry. Any unauthorized user can take over at any point after.

FRICTION TO ADOPT
Standards such as Multi-Factor Authentication, Passwords and Shared Secrets take valuable time and add friction to the user’s experience.

ONE SIZE FITS ALL
Session security after access are often automatic timeouts. It leaves the user vulnerable up until timeout and they’re a headache once the user is back, having to log back in.

YOURBIOMETRICS ARE ACCESS TO INFORMATION
PERSISTENTLY
THE PUA IMPACT


IMPROVE USER EXPERIENCE
Increase the number of successfully authenticated legitimate users

THWART FRAUD
Prevent account takeovers with more secure authentication

REDUCE COST
Unlimited-use pricing model enables cost reduction and deployment across use cases.

ZERO TRUST WITH PASSWORDS
- Low to Moderate Levels of Assurance (LOA)
- Higher operational costs
- Gaps in MFA adoption
- Vulnerable to credential-based attacks
- Slower overall program rollout
- Constraints on IT infosec resources
ZERO TRUST WITHOUT PASSWORDS
- High levels of assurance (NIST AAL3)
- Lower operational costs
- Rapid scaling of MFA adoption
- Resistant to phishing and credential-based attacks
- Accelerated program cycles
- Reduce IT/IAM resource constraints

NO PASSWORDS, NO SHARED SECRETS, NO FRICTION
Strengthen your organization’s security while making it faster and easier for stakeholders to access digital systems and resources from anywhere
Be confident only authorized users are accessing company devices with PUA Continuous Endpoint Authentication.


PUA prevents device sharing, ensuring each person in front of their device is the true authorized user
So regardless if they decide to intentionally share their device, or if someone tries to sue their device without their knowledge– the result is the same. PUA spots the intruder and takes instant action to lock the session and secure the information.
VULNERABILITY ISN’T JUST A HUMAN FACTOR
Hacking Technologies are Emerging Threats
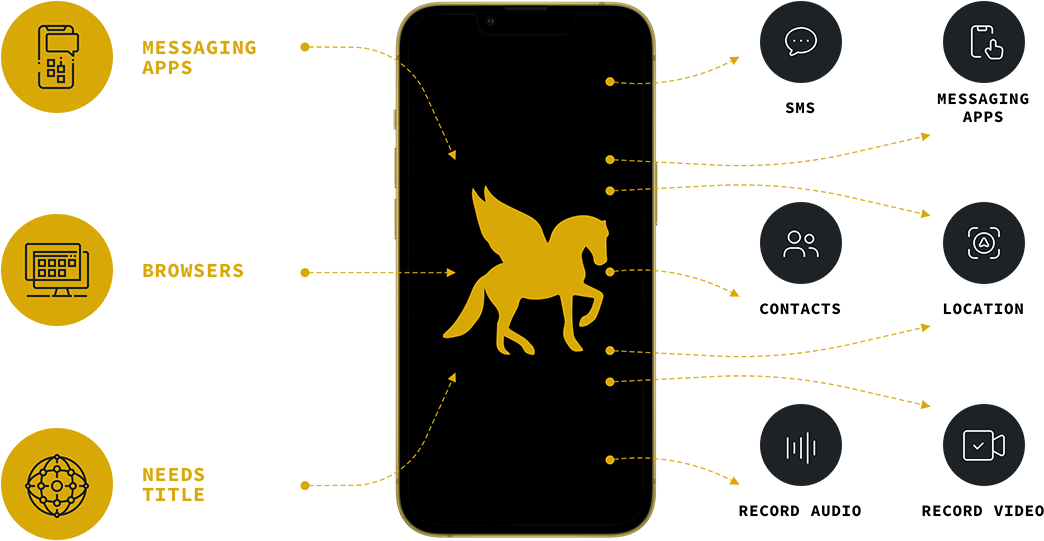
In recent years, there has been a growing concern over the use of spyware and surveillance tools that can be used to monitor individuals and their digital activity. One of the most infamous examples of such spyware is Pegasus, a powerful tool created by the Israeli NSO Group. Pegasus has been used by various governments around the world to spy on journalists, activists, and other individuals deemed to be a threat.
IT’S TIME TO DEPLOY PHISHING RESISTANT AUTHENTICATION
End the unacceptable trade-off between security assurance and a frictionless user experience with PUA from The Whisper Co.
RESOURCES

Download our PUA whitepaper, explaining why PUA is the natural progression for authentication and secure access.




