THE THREAT
CURRENT SOLUTIONS AREN’T CUTTING IT
HACKING

A significant and well-known threat to information privacy and security involves hacking. It is the deliberate and unauthorized intrusion into computer systems or networks to exploit vulnerabilities, gain control, steal data, or disrupt operations.
Hackers use various techniques, including malware, phishing attacks, software like Pegasus, SIM-swapping, or exploiting software vulnerabilities, jeopardizing the confidentiality, integrity, and availability of sensitive information.
By implementing i2i encryption, invisible-ink prevents hackers to gain access to your information. The information remains encrypted at-rest in your device, so hackers can only harvest cipher data.

IMPROPER SHARING

A significant and well-known threat to information privacy and security involves hacking. It is the deliberate and unauthorized intrusion into computer systems or networks to exploit vulnerabilities, gain control, steal data, or disrupt operations.
Hackers use various techniques, including malware, phishing attacks, software like Pegasus, SIM-swapping, or exploiting software vulnerabilities, jeopardizing the confidentiality, integrity, and availability of sensitive information.
By implementing i2i encryption, invisible-ink prevents hackers to gain access to your information. The information remains encrypted at-rest in your device, so hackers can only harvest cipher data.

UNAUTHORIZED ACCESS

A significant and well-known threat to information privacy and security involves hacking. It is the deliberate and unauthorized intrusion into computer systems or networks to exploit vulnerabilities, gain control, steal data, or disrupt operations.
Hackers use various techniques, including malware, phishing attacks, software like Pegasus, SIM-swapping, or exploiting software vulnerabilities, jeopardizing the confidentiality, integrity, and availability of sensitive information.
By implementing i2i encryption, invisible-ink prevents hackers to gain access to your information. The information remains encrypted at-rest in your device, so hackers can only harvest cipher data.

SPOOFING

A significant and well-known threat to information privacy and security involves hacking. It is the deliberate and unauthorized intrusion into computer systems or networks to exploit vulnerabilities, gain control, steal data, or disrupt operations.
Hackers use various techniques, including malware, phishing attacks, software like Pegasus, SIM-swapping, or exploiting software vulnerabilities, jeopardizing the confidentiality, integrity, and availability of sensitive information.
By implementing i2i encryption, invisible-ink prevents hackers to gain access to your information. The information remains encrypted at-rest in your device, so hackers can only harvest cipher data.

SHOULDER SURFING

A significant and well-known threat to information privacy and security involves hacking. It is the deliberate and unauthorized intrusion into computer systems or networks to exploit vulnerabilities, gain control, steal data, or disrupt operations.
Hackers use various techniques, including malware, phishing attacks, software like Pegasus, SIM-swapping, or exploiting software vulnerabilities, jeopardizing the confidentiality, integrity, and availability of sensitive information.
By implementing i2i encryption, invisible-ink prevents hackers to gain access to your information. The information remains encrypted at-rest in your device, so hackers can only harvest cipher data.

WHAT IS INVISIBLE-INK [i-i]?

PRIVACY & SECURITY BY DESIGN & DEFAULT
- With the invisible ink app, you can guarantee that only authenticated individuals have access to the content you send.
- With invisible-ink, you have the guarantee that only an authorized user could have sent you the message
- Contents stay invisible to everyone else viewing the app
- This innovation introduces a new level of ownership and security to communication channels.
KEY BENEFITS OF INVISIBLE-INK
No More Spoofing
No More Hacking
No More Improper Sharing
No More Unlocked Device Vulnerability
No More Unauthorized Access
No More Unauthorized Access
Active Protection against man-in-the-middle attacks
Backdoors
At-Rest Encryption
Keys stay on device
COMPLETE PROTECTION
[ZERO TRUST BY DESIGN & BY DEFAULT]
FYEO: FOR YOUR EYES ONLY
For Your Eyes Only (FYEO) is a paradigm shift from authentication one-time for access. FYEO ensures that only authorized users are able to access, view and edit contents continuously. It ensures with trust, who is the sender and receiver.
i2i ENCRYPTION
The only messaging app with eyes-only privacy. Anything shared over invisible-ink stays encrypted not only in transit, but at-rest, on the recipient’s device. It is only decrypted when the authorized user is viewing. Real-time decryption.
OWNERSHIP
A new level of ownership in communications. With invisible-ink you can redact messages, send them self-destruct, set custom sharing preferences to eliminate forwarding, printing, and more. True Ownership is here!
SHOULDER SURFING
Shoulder Surfing a.k.a. Visual Hacking is the act of someone viewing the contents of someone else’s screen. For additional security & privacy, invisible-ink has multiple face detection, obfuscating the information when visual hackers are detected. Shoulder Surfing protection is here.
POWERED BY PATENTED PERSISTENT USER AUTHENTICATION
FYEO: FOR YOUR EYES ONLY
For Your Eyes Only is a level of privacy and security that we enable by leveraging our patented Persistent User Authentication. It enables trust beyond any other platform. Perfect identity assurance that only authorized users can send, view and edit contents therein.


If the authorized user is in front of their device the contents are visible


If the authorized user walks away and is not in front of their device the contents are invisible.
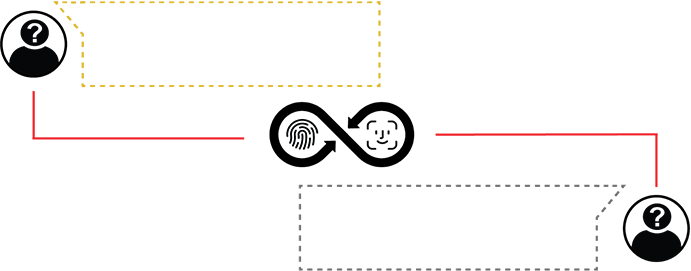


ABOVE THE STANDARD END-TO-END ENCRYPTION [E2E]
PROPRIETARY EYE-TO-EYE ENCRYPTION [i2i]
While many messengers offer end-to-end encryption, safeguarding information solely between devices, decrypting when it arrives at the recipient’s device. Our eye-to-eye encryption takes security to a higher level. Not only does it keep data encrypted between devices, but maintains it encrypted after the information reaches the device, decrypting only when the authorized user’s eyes are focused on the screen.
In the absence of the authenticated user, the information remains securely encrypted, offering protection against spyware and preventing (remote) hackers from accessing any (decrypted) information. Since the encryption keys are paired peer-to-peer and only authorized users can use the app to send messages, spoofing and impersonation is avoided.
OUR ENCRYPTION VS. THEIRS
Theirs:
- e2e (end-to-end) Encryption
- No Encryption at-rest
- No Real-Time Decryption
- No Biometric to Unlock or Use by Default
- No Privacy & Security by Design & Default
Ours:
- i2i (eye-to-eye) Encryption
- Encryption at-rest
- Real-Time Decryption
- Biometric to Unlock (Access and Use) by Default
- Privacy & Security by Design & Default
MORE THAN JUST ENCRYPTION
BRINGING TRUE OWNERSHIP TO YOUR COMMUNICATIONS
We hold the belief that as information creators, we should possess the authority to determine the usage, display, and accessibility of our content as owners. Ownership is the focal point of this principle. To empower our users with such ownership, we have developed various features.
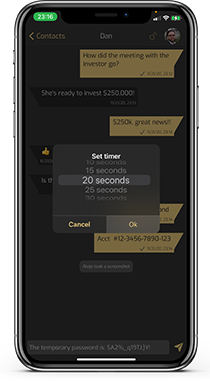
EPHEMERAL (SELF-DESTRUCT)
Restrict how long a message is present for the recipient to view. Once the timer goes off, the message will delete from both your and the recipient’s devices.
MESSAGE REDACTION
Restrict how long a message is present for the recipient to view. Once the timer goes off, the message will delete from both your and the recipient’s devices.
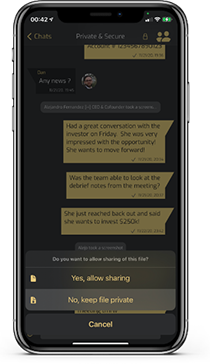
CUSTOM SHARING PREFERENCES
Restrict how long a message is present for the recipient to view. Once the timer goes off, the message will delete from both your and the recipient’s devices.
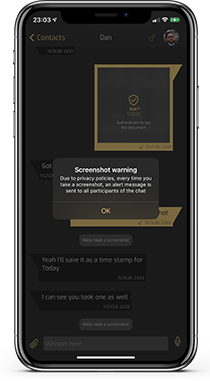
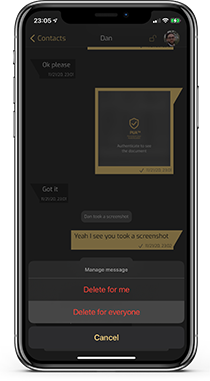
SCREENSHOT PROTECTION
Restrict how long a message is present for the recipient to view. Once the timer goes off, the message will delete from both your and the recipient’s devices.

YOU OWN YOUR KEYS
Restrict how long a message is present for the recipient to view. Once the timer goes off, the message will delete from both your and the recipient’s devices.

SCREENS NEED PROTECTION
SHOULDER SURFING
Shoulder surfing, visual hacking, or visual eavesdropping is a problem that is not currently being addressed. Invisible-Ink offers an additional layer of security, giving shoulder surfing protection to invisible-ink users.
STUDIES [REFERENCE SOURCE] HAVE SHOWN
of visual hacking attempts globally were successful in capturing sensitive information.
of visual hacking was not stopped by employees.
of visual hacks occurred in less than 15 minutes, and 66% occurred in less than 30 minutes.
To enhance privacy and security, invisible-ink incorporates an additional layer of protection through its second face detection feature. This feature can be activated to thwart shoulder surfing and prevent successful visual hacking attempts. Once a second face is detected, invisible-ink will obscure the screen, allowing only the authorized user to view its contents when they are alone in front of the device. The user has the option to enable or disable this feature as per their preference.
WHERE SECURE ACCESS REALLY MATTERS
USE CASES
When For Your Eyes Only (FYEO) communication become paramount
DOCUMENT HANDLING
Secure document sharing & viewing.
INVESTIGATIVE JOURNALIST
Identity assurance of sources and information.
HUMAN RIGHTS ACTIVISTS
Security of conversations and content shared.
PSYCHOLOGISTS
Privately exchanging sensitive information with patients.
NATIONAL DOMESTIC VIOLENCE HOTLINE
Secure messaging for victims.
GOVERNMENT AGENCIES
Department of Health and Human Services.
MILITARY
Securing access to sensitive information.
REMOTE WORKING
Eliminating improper sharing and shoulder-surfing.
1ST AMENDMENT
We protect privacy, security and freedom of speech as they are human rights.
OPPRESSIVE REGIMES
Protecting dissidents from police states and corrupt governments.
PRIVACY BY DEFAULT, SECURITY BY DESIGN
ALWAYS FREE FOR PERSONAL USE
Invisible-Ink is and always will be free for individual users.
DO YOU NEED A PRIVATE LABEL VERSION?

The full invisible-ink platform is also available as a white label / private label / custom branded platform, and can run on your private network.

CONCEPTION OF INVISIBLE-INK
OUR ORIGIN STORY & ABOUT TWC

Our founders are from Latin America, which has had its share of oppressive regimes over the last century. In these regimes, security forces can stop a citizen and “force” them to use their biometrics to gain access to their devices. They can look at the information stored in the device and if they don’t like it, they can create a false narrative (false charges) to justify their incarceration, silence them or destroy their reputation and credibility. These are not only theoretical statements, but have happened to some of our founders’ family members in Venezuela.
A particular case is Manuel Alejandro or Manu for short, a cousin of the co-founders. He was the Director of International Relations of Interim President of Venezuela, Juan Gerardo Guaidó Márquez; Manu had to hide in a Chilean embassy because of false charges and to avoid incarceration and was always worried about his communications.
That’s why we created Invisible-ink. It was our way of paying our technology forward to those that need it most, specially those where privacy and security are a matter of life and death, like Manu. Ultimately, we want this technology in every phone, helping in our mission to build a more trustworthy digital world.
PRIVACY AND SECURITY ARE HUMAN RIGHTS
PRIVACY IS NON-NEGOTIABLE

As individuals, we value our data and privacy, desiring complete control over them. With Invisible-Ink, your data remains exclusively stored on your mobile device. The Whisper Company, with Invisible-Ink, ensures that no one has access to your data, even us.
You retain full authority over who can access your data, and in the event you choose to share it, you have the power to revoke access by erasing it from your device and any other devices you’ve shared it with, whenever you wish.
We adhere to the 1st amendment and believe you can’t negotiate your rights. We protect your data as if it is a matter of life or death. Privacy and security are invaluable human rights and we protect them as such.
IN THE NEWS
THE PULSE OF SECURE COMMUNICATION
Oppressive Regimes & Freedom of Speech
In authoritarian regimes, personal privacy is invaded, dissent is silenced, and activists rely on encrypted communication and anonymous browsing to fight for freedom and human rights.
Mobile Insecurity: A Growing Threat to Personal and Professional Safety
Smartphones have become essential in our lives, but their vulnerability to cyber attacks poses a serious threat.
It's OK to be Paranoid
In a world where cybersecurity breaches are on the rise, paranoia might just be your best defense—explore why it’s okay to be paranoid about cybersecurity and learn crucial steps to protect yourself in this insightful blog post.
GET IN TOUCH
Investment, Product and Technology Questions or Requests?
Reach out and we’ll gladly respond

